Using the Firewall Editor
The Firewalling Overview page displays all the firewall rule groups used by servers in your account, and any firewall rule groups that are not currently in use. You can click "Edit" to amend the rules contained within firewall rule group;
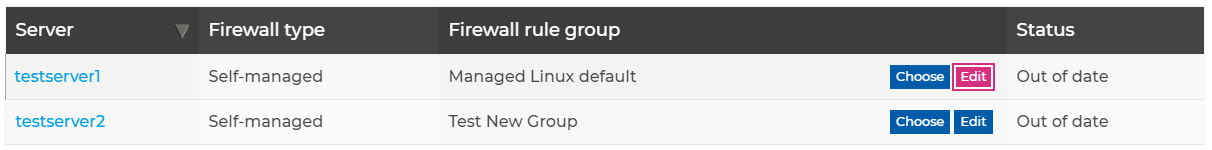
Once you have selected the rule group to edit you are taken to the editor page which will show you any existing rules in place, and give you the options to edit the rule group further;
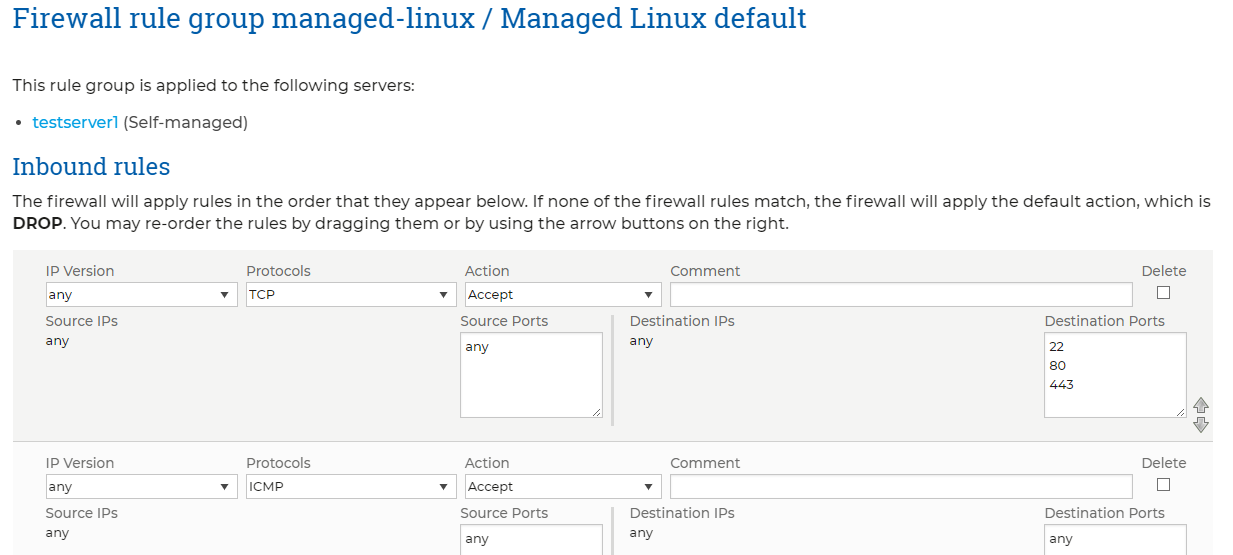
You will have options to specify any Inbound rules and Outbound rules for the Rule Group.
The rules in the editor are divided horizontally and vertically. with each individual Firewall Rule contained within its own "Box" (alternately coloured for easier differentiation). The items contained within each rule are the configurable aspects of the rule, these are as follows;
- IP Version – The IP Version that this rule applies to, you can select either;
- IPv4
- IPv6
- Any - The “any” option specifies both IPv4 and/or IPv6.
- Protocols - These are the Protocol types that can be filtered for. There are various options available to select. The most common are:
- TCP - The standard packet type that most data on the Internet is exchanged with.
- UDP - Another common protocol used most commonly with DNS requests (on port 53) and media streaming.
- ICMP - Otherwise known as a “Ping Packet”
- Action - This indicates what action the firewall will take when an incoming packet matches this rule. The options are:
- Accept - The packet is allowed to progress to the server
- Drop - The packet is silently deleted
Reject - The packet is returned to the sender
Drop is usually selected to deny packets because it does not provide any additional information to an attacker. A rejected packet indicates to the attacker that the IP address is in use and something is listening whereas when a packet is dropped it looks to the attacker like there is nothing there.
- Comment - This is an optional field and is a space to leave a note regarding the rule, useful for keeping track of what a rule does or why it was added. This field can be left blank where required.
- Delete - Check this box to delete the selected rule when changes to the Rule Group are saved.
- Source IPs - This is the IP address(es) of the machine(s) that would send the packet. A single IP or IP range can be entered here, but only in CIDR notation e.g. "1.2.3.4/24"
- In this field, the value "Any" indicates every IP address on the internet.
- Please see Wikipedia for an explanation of CIDR notation.
- Please see here for an online CIDR calculator.
- Destination Ports - These are the port or ports that the packet is bound for on your server. For example, a request for a web page will be on port 80.
The Common Port and their Uses Page, provides some details on various common ports that you may want to use or allow access to.
Port Ranges can be specified for large ranges of ports. They have the form first-port colon last-port e.g. 20:22 or 49152:65534 etc, this is the same as manually entering each port individually so for "20:22" this would be ports, 20, 21 & 22.There is a limit of 15 ports per firewall rule. A port range e.g. 20:22 counts as two ports towards this limit. If you have more than 15 ports, you will need to create an additional rule.
- Destination IP - This is the IP or IPs of your server. This allows you to create different rules for your server's IPs if it has more than one. or the Rule Group is applied to multiple servers.
- In this field the value "Any" indicates all your server's IPs.
- A single IP or IP range can be entered here, but only in CIDR notation e.g. "1.2.3.4/24"
- Destination Ports - These are the port or ports that the packet is bound for on your server. For example, a request for a web page will be on port 80.
The Common Port and their Uses Page, provides some details on various common ports that you may want to use or allow access to.
Port Ranges can be specified for large ranges of ports. They have the form first-port colon last-port e.g. 20:22 or 49152:65534 etc, this is the same as manually entering each port individually so for "20:22" this would be ports, 20, 21 & 22.There is a limit of 15 ports per firewall rule. A port range e.g. 20:22 counts as two ports towards this limit. If you have more than 15 ports, you will need to create an additional rule.
The firewall will apply rules in the order that they appear in the Firewall Editor, more information on this can be found in the "How the Firewall Works and Rule Ordering" page. You can re-order the firewall rules by dragging them (from the left hand side border) or by using the arrow buttons in the bottom right of the .
- For Inbound Rules, if none of the firewall rules match, the firewall will apply the default action, which is DROP.
- Internal Traffic (i.e. Traffic between two servers in a VLAN) is not affected by the Firewall Rules listed here.
After the Inbound and Outbound rules, you can then save the changes to your Rule Group, you will have an option to specify the following;
- Nickname - This is your own short name for the Firewall Rule Group that can be used to identify the Rule Group.
- Default Outbound Policy - The default policy to be applied to any Traffic (the default option is set to "Accept").
- Notes - An optional free text field to allow you to specify any notes for the Firewall Rule Group.
- Change Log Comment - An optional free text field to add a comment describing the changes made. This comment will be displayed in the "Recent rule group changes" change history section.
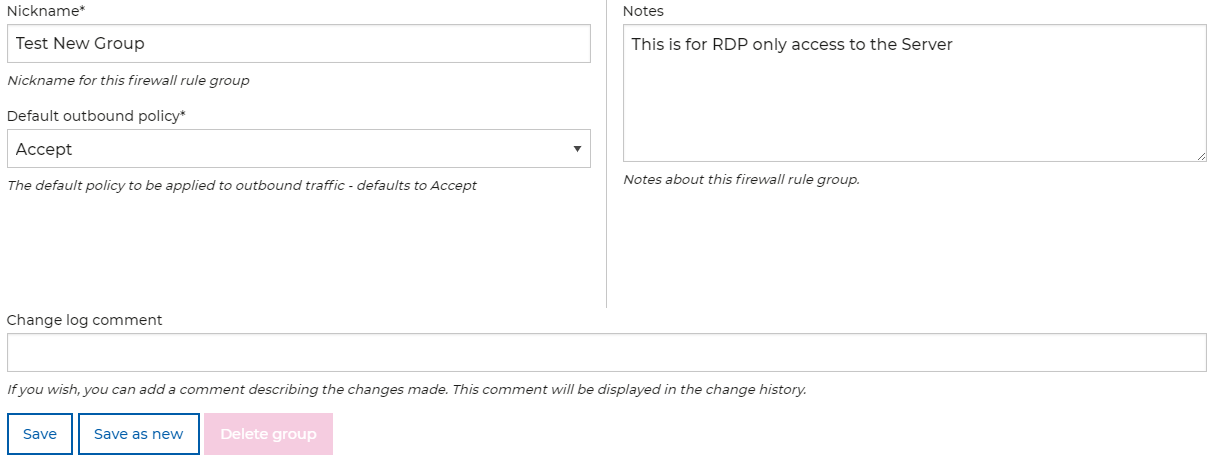
Once all fields have been entered you can then press "Save" to Save any changes to your Rule Group, or "Save as New" that will allow the rule group to be saved to your account as a new Rule Group with the changes made.
If the Rule Group is not in use with any Servers or Services, you can press the "Delete" button to delete the Rule Group from your account (Note: This action can't be reversed).
Changes to the Firewall Rule Group are applied the next time the Firewall Reloads, this is typically once every 30 minutes.
Change History
At the bottom of the Page for any existing custom Rule Group, you will have a "Recent rule group changes" section, this will show a table with details on any changes to the Firewall Rule Group, including any Change Log Comments provided. An example of this can be seen below;
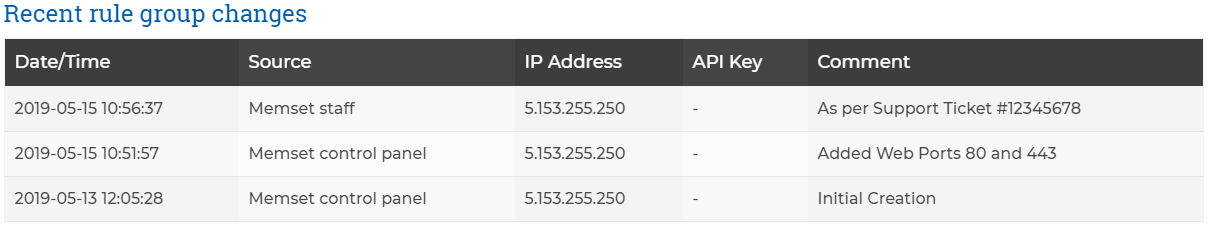
This shows the following information;
- Date/Time - Date and Time the change was made (all times are in UTC),
- Source - The Source of the change ("Memset Control Panel" or "API" or "Memset Staff" etc),
- IP Address - the IP Address from where the changes originate,
- API Key - The API Key used to make the change
- Comment - Any Change Log Comment provided at the time of the change.